top of page
All Posts


Beyond the Penetration Test: What is a Red Team Engagement and Why Do You Need It?
Most organizations confuse penetration testing with red teaming, but the difference could be the gap an attacker needs. Discover what a Red Team engagement actually entails, why it’s the ultimate stress test for your "Blue Team," and how to determine if your security posture is mature enough to handle a full-scale adversarial simulation.
Dereck Coleman
Feb 104 min read

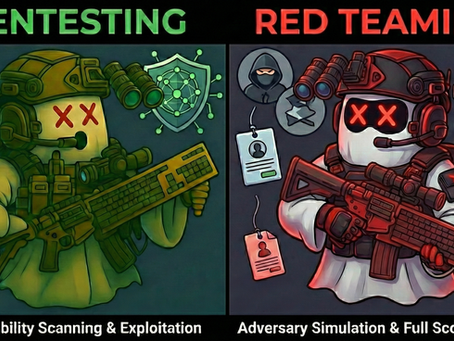
Find the Flaw or Fight the Threat? Decoding Pentesting vs. Red Teaming
Find the flaw or fight the threat? We decode the critical differences between Pentesting and Red Teaming to help you build a resilient defense.
Dereck Coleman
Jan 184 min read


Chasing the Ghost in the Machine: Mastering SSRF with Ghost Ops Security
"In cloud-native architectures, Server-Side Request Forgery (SSRF) lets attackers turn servers into proxies, bypassing defenses to reach internal networks and cloud metadata.
This deep dive explores common SSRF entry points, advanced exploits like credential exfiltration and protocol smuggling, bypass techniques (IP encoding, DNS rebinding, redirect chaining), and how tools like ghostsurrrfs automate discovery and exploitation.
Dereck Coleman
Jan 52 min read


F5 BIG-IP Breach: Why Attackers Now Have Your Blueprint — And What to Do Before the Exploits Drop
A newly exposed vulnerability in F5's BIG-IP systems has opened the door for attackers to gain full remote control—no credentials required. This breach underlines the urgent need for proactive offensive security testing. Ghost Ops breaks down what went wrong, who’s at risk, and how to defend your perimeter before attackers do it for you.
Dereck Coleman
Oct 17, 20253 min read


File Upload Vulnerabilities: The Silent Breach Vector Hiding in Plain Sight
File upload vulnerabilities are one of the most dangerous and overlooked security gaps in web apps today. Learn how attackers exploit them to gain RCE and shell access — and how Ghost Ops uses real-world tools like file_uploader.py to test and defend your most critical upload endpoints.
Dereck Coleman
Oct 4, 20254 min read


Essential Reasons Why the Healthcare Industry Must Prioritize Penetration Testing Against Cyber Threats
In today’s digital landscape, healthcare organizations increasingly depend on technology to handle patient data and improve operational...
Dereck Coleman
Sep 24, 20254 min read


Understanding Ghost Ops Security in Modern Cyber Defense
In today’s digital battlefield, threats evolve fast. Attackers probe relentlessly. Defenders must respond faster. Ghost Ops Security is...
Dereck Coleman
Sep 16, 20254 min read


XPath Injection: A Tactical Guide
Discover how attackers exploit XPath Injection vulnerabilities in XML-based web applications to bypass authentication, extract sensitive data, and compromise backend systems. Learn attack methods, real-world payloads, and mitigation tactics in this tactical deep dive from Ghost Ops Security.
Dereck Coleman
Sep 12, 20253 min read


Why CyberSecurity Testing Matters for Your Organization
In this blog post, we delve into the critical importance of mastering cybersecurity testing techniques such as vulnerability scanning, penetration testing, and risk assessment. Discover actionable steps for organizations to fortify their defenses and the significant advantages of partnering with Ghost Ops Security for expert guidance in safeguarding your business.
Dereck Coleman
Sep 9, 20254 min read


CVE-2025-6554: Understanding the Vulnerability and Its Impact
Google Chrome’s latest zero-day, CVE-2025-6554, is a type confusion flaw in the V8 engine that’s already being exploited in the wild. In this post, Ghost Ops breaks down how attackers leverage it, what our PoC revealed, and why immediate patching is critical for business risk management.
Dereck Coleman
Aug 27, 20253 min read


Beyond Human Hackers: State-Sponsored AI in the Shadows
The global threat landscape has shifted. State-sponsored cyber actors are no longer just deploying human operators — they’re embedding...
Dereck Coleman
Aug 24, 20253 min read
bottom of page
